Since our inception in 2002, Thru has always taken security of our product and our customers’ data very seriously. We transfer sensitive data for corporations on a daily basis and must meet tightening data privacy regulations and guard against the everchanging and continually growing number of cybersecurity threats.
As such, we are always open to evaluations of our product and information security (InfoSec) from trusted third parties.
This past summer, we agreed to an assessment by CyberVadis at the request of one of our current customers. This Cybersecurity and Data Privacy Performance evaluation of Thru covered areas such as infrastructure, personnel, product development…everything!
Continue reading for a quick overview of CyberVadis and how they provide assessments. To see our CyberVadis Cybersecurity and Data Privacy Performance report, please contact your account representative.
Who Is CyberVadis?
How CyberVadis Evaluates Security Risks of Third-Party Vendors
CyberVadis provides logins to a vendor’s representatives so they can directly access a secure online portal containing questions with multiple choice answers. The portal provides users access to an in-depth questionnaire covering four focus areas of security practices, procedures and policies and four categories of functions across the focus areas:
Focus Areas
- Data privacy
- Data protection
- Business continuity
- Third-party security management
Function Categories
- Identify
- Protect
- Detect
- React
For each selected answer choice, the user is required to upload and submit supporting evidence, such as policy statements, procedure manuals, inventory spreadsheets and screenshots. The platform allows users to navigate through the questions in any order and provides instructions, tips and examples of appropriate evidence for each answer.
After the vendor completes the questionnaire by a specified date, the expert analysts at CyberVadis manually and rigorously audit the submitted proof to validate and confirm the security claims of the vendor organization. CyberVadis then issues a report that includes results assessment and a standardized cybersecurity rating that can be shared with others. The report also includes improvement recommendations for the vendor.
CyberVadis cybersecurity ratings scale:
| INSUFFICIENT | BASIC | MODERATE | DEVELOPED | MATURE | <400 | 400-549 | 550-699 | 700-849 | >850 |
|---|
Thru’s Cybersecurity and Data Privacy Performance Overview
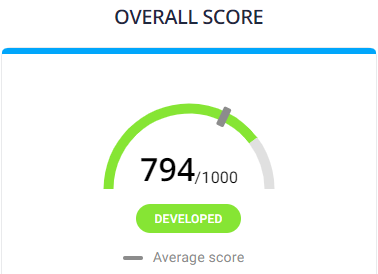
After CyberVadis received, analyzed and validated our answers with accompanying proof, our overall score of 794 placed us in the DEVELOPED category.
Identify Function Scoring
The Identify function consists of identifying sensitive assets that should be protected and their risks. Additionally, deciding what needs to be implemented to cover the major risks.
Thru scored 904 (Mature) overall in Identify, which is evaluated across the categories of
- Compliance
- Data privacy
- Governance
- Asset management
- Risk assessment
- Human resources

Protect Function Scoring
The Protect function includes implementing security measures that will contribute to limit or contain the impact of a potential cybersecurity event.
Thru scored 758 (Developed) overall in Protect, which is evaluated across the categories of
- Access management
- Information protection
- Network management & mobility security
- Security in projects & applications development
- Infrastructure security
- Physical protection
- Third-party management
- Awareness & training

Detect Function Scoring
The Detect function includes developing and implementing the appropriate measures to identify the occurrence of a cybersecurity event.
Thru scored 809 (Developed) overall in Detect, which is evaluated across the categories of
- Logging & monitoring
- Detection process
- Anomalies & events

React Function Scoring
The React function includes developing and implementing the appropriate measures to take action regarding a detected cybersecurity event.
Thru scored 732 (Developed) overall in React, which is evaluated across the categories of
- Incident management
- Crisis management
- Improvements

Thru’s Complete Results of Third-Party InfoSec Review
We are pleased with our results and rating. Additionally, we are now aware of very specific areas that need improvement and have guidance on how to implement and achieve those standards or practices.
If you are considering Thru for managed file transfer for your business and would like to see our CyberVadis Cybersecurity and Data Privacy Performance report, please contact your account representative.